In any modern operating system when you login, you are greeted with a login screen asking for your credentials. If you are the only user using the system, you may be spared the labor of filling in the username, but a password still will be required to login.
We can forgo the exercise of filling the password by virtue of asymmetric encryption. Asymmetric encryption makes two types of keys available – private and public. As the name suggests, public key can be made available to the public while the private key remain with the system which needs to do the authentication. In our case we will be logging into Raspberry Pi using SSH and will use key based authentication mechanism to login, forgoing the need of any password. Pi will send the public key over the wire to the host operating system running Putty which will then compare it with the companion private key. If a match is found, the user authenticates successfully. Note that the private keys never travels over the wire.
We need the following to make this a possibility:
1. PutTTYgen: To generate a pair of keys,
2. Pageant: To run in the background and maintain availability of the private key
Both the aforementioned software components come bundled with Putty, so if you have Putty installed, there’s a good chance that they are already installed on your system.
Generating a key pair
Open PuTTYgen and click on the “Generate” button generate a pair of keys. Make sure that “RSA” algorithm is selected with key strength of 2048 bits. Once generated, use the in-built facility and save the public and private keys to the folder which you consider save enough to retain your private key for future reference. DO NOT SHARE YOUR PRIVATE KEY WITH ANYONE.
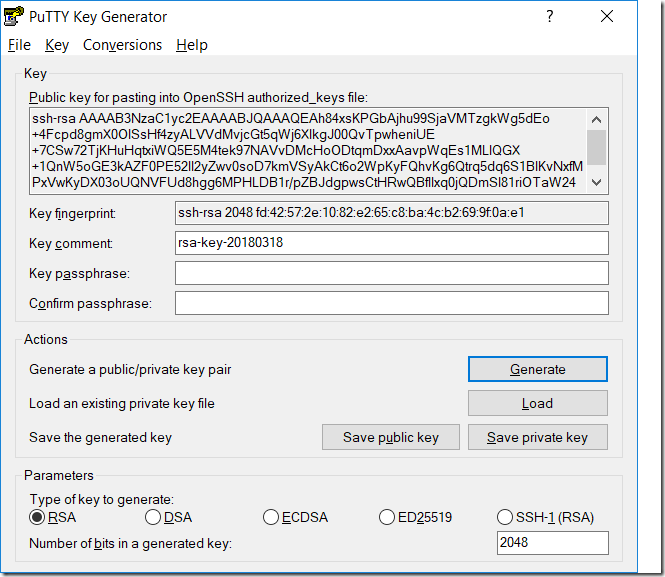
Now, the most important part. If you look at the format of the public key saved by PuTTYgen, you will find that it spawns multiple lines. It is un-usable in majority of the systems and exists only for reference. We need to copy the public key in the large “Key” window, which specifically makes the key properly formatted for use in OpenSSH based authentication systems.
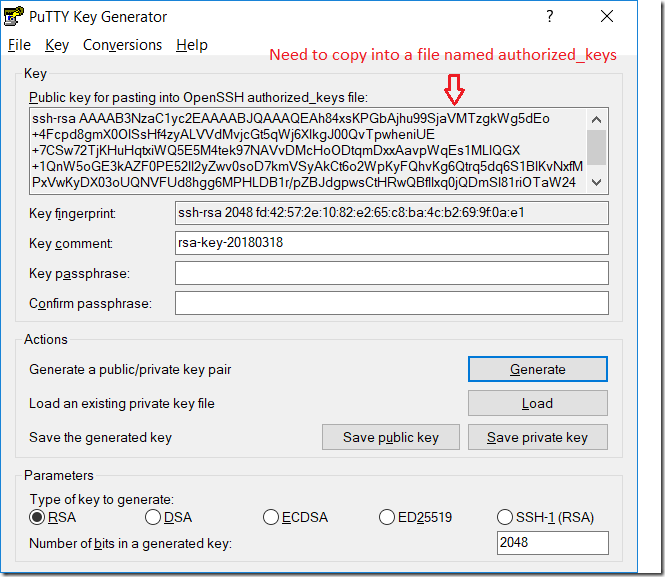
Copy the key into a simple text file and name it “authorized_keys” and remove the txt extension. This is the file that will be used by Raspbian Stretch operating system without any further configuration.
Now run the Pageant agent in your Windows system and add the private key generated previously. The private key should have an extension “ppk”. Pageant agent will run on the host operating system where from you want to connect and will keep the private key handy.
Configuring Raspberry Pi
Now let’s configure our Raspberry Pi to accept key based authentication. Login the usual route with your username and password and follow the steps:
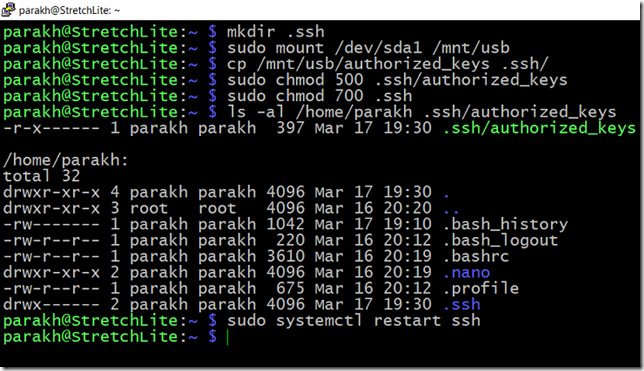
1. Create a .ssh folder (hidden folder) in the home directory of the user for whom you want to use key based authentication.
2. Copy over the public key (NOT PRIVATE KEY) that you generated previously and named “authentication_keys” to the folder. I used a thumb drive for the purpose.
3. Secure the key file and the .ssh folder. Only the user meant to use the key based authentication should be able to access the key file in read-only and executable capacity. The .ssh folder should be off limits to everyone else.
4. Restart the ssh service.
5. Logout and log back in with the username for which you enabled the key based authentication.
mkdir .ssh
sudo mount /dev/sda1 /mnt/usb
cp /mnt/usb/authorized_keys .ssh/
sudo chmod 500 .ssh/authorized_keys
sudo chmod 700 .ssh
ls -al /home/parakh .ssh/authorized_keys
sudo systemctl restart ssh
All this was made possible by the magic of asymmetric encryption.
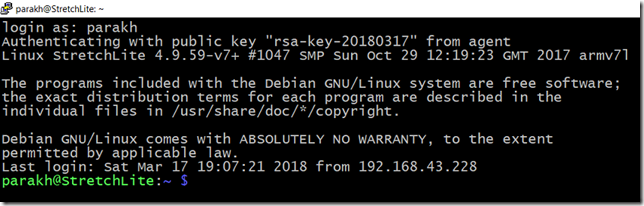
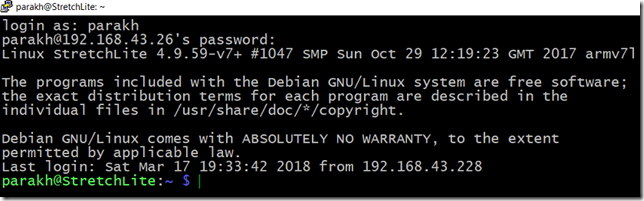
The good thing about this scheme is that if, for some reason the public key on Raspberry Pi gets corrupted, or the Pageant is not running in the background on the host operating system, then you get offered the good-old password challenge. I purposely exited the Peagent and as expected Pi challenged me with a password corresponding to my account.
References:
1. Passwordless SSH access